

Peering agreements are contracts between internet service providers (ISPs) or networks to exchange traffic directly without having to pay a third-party network for the transit of data. These agreements impact internet traffic exchange by allowing networks to interconnect and share traffic more efficiently, reducing the need to route data through multiple intermediaries, which can lead to faster and more reliable connections for end-users.
Tier 1 ISPs utilize peering agreements to improve network performance by establishing direct connections with other Tier 1 networks or large content providers. By peering directly with other major networks, Tier 1 ISPs can reduce latency, increase bandwidth capacity, and enhance overall network reliability. This direct interconnection helps in delivering a better quality of service to their customers.
Connected and live within 10 working days: The Real Greek in Paradise street Liverpool has now been connected at Gigabit speeds to Baltic Broadband’s 100Gbps fibre network that circles Liverpool...
Posted by on 2024-01-22
Our team at Baltic Broadband really enjoyed working on Paramount’s eagerly awaited original drama series Sexy Beast, which has now been released! Facilitated by the Liverpool Film Office, the production...

Posted by on 2024-01-09
Baltic Broadband have today launched Liverpool City Region Data Centres (LCRDC) as a separate brand to it’s Broadband business. Previously, offering Data Centre space had been a service that has...
Posted by on 2024-01-08
For years, Escape Live struggled with poor performing broadband from the national providers. After waiting almost 2 years for them to deliver a fast and reliable product, they lost patience...

Posted by on 2024-01-03
The key differences between settlement-free peering and paid peering agreements lie in the financial aspect of the arrangement. Settlement-free peering involves networks exchanging traffic without any monetary compensation, based on the principle of mutual benefit. On the other hand, paid peering agreements involve one network paying another for the privilege of exchanging traffic directly, usually to ensure a certain quality of service or to handle high traffic volumes.

Content delivery networks (CDNs) benefit from peering agreements with ISPs by improving the delivery of content to end-users. By establishing peering connections with ISPs, CDNs can reduce latency, decrease the load on their own network infrastructure, and enhance the overall user experience. This direct interconnection allows CDNs to deliver content more efficiently and reliably to users across different networks.
Internet Exchange Points (IXPs) play a crucial role in facilitating peering agreements between networks by providing a physical location where multiple networks can interconnect and exchange traffic. IXPs act as neutral meeting points where ISPs, CDNs, and other networks can peer with each other, enabling more efficient data exchange and reducing the reliance on third-party transit providers. This direct interconnection at IXPs helps in improving network performance and reducing costs for participating networks.
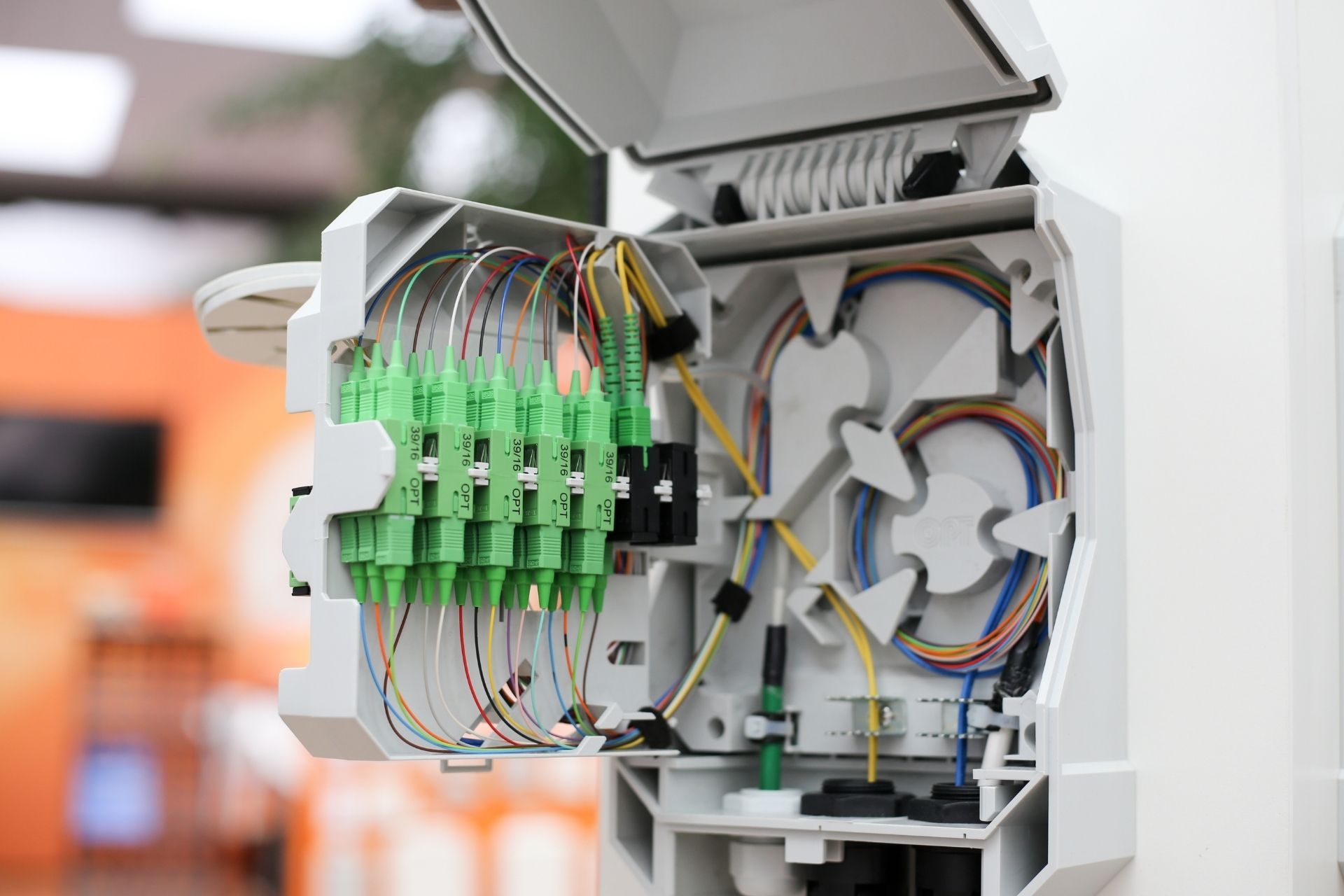
Peering agreements contribute to reducing latency and improving overall network efficiency by enabling direct interconnection between networks, bypassing the need to route traffic through multiple intermediaries. This direct exchange of traffic allows for faster data transmission, lower latency, and increased bandwidth capacity, leading to a more seamless and reliable internet experience for end-users. By peering with other networks, organizations can optimize their network performance and enhance the quality of service they provide to customers.
Some common challenges faced by networks when negotiating peering agreements include disagreements over traffic ratios, differences in network size and capacity, concerns about network security and privacy, and the complexity of technical requirements for establishing direct interconnections. Networks may also face challenges related to the financial aspects of peering agreements, such as determining fair pricing structures or negotiating terms that are mutually beneficial. Overcoming these challenges requires open communication, collaboration, and a willingness to find common ground to ensure successful peering arrangements.

Bulk internet providers utilize a variety of advanced techniques to mitigate DDoS attacks and ensure the stability and security of their networks. These techniques may include deploying dedicated DDoS mitigation hardware and software, such as firewalls, intrusion detection systems, and traffic scrubbing tools. Additionally, providers may implement rate limiting, access control lists, and traffic filtering to identify and block malicious traffic. Some providers also utilize cloud-based DDoS protection services to quickly scale up their defenses in the event of a large-scale attack. By continuously monitoring network traffic and analyzing patterns, bulk internet providers can proactively detect and mitigate DDoS attacks to minimize their impact on their infrastructure and customers.
When designing and architecting a bulk internet data center, it is essential to follow best practices to ensure optimal performance and efficiency. This includes considering factors such as scalability, redundancy, security, and energy efficiency. Utilizing high-density servers, virtualization technology, and cloud computing can help maximize space utilization and reduce energy consumption. Implementing a robust network infrastructure with redundant connections, firewalls, and intrusion detection systems is crucial for protecting data and ensuring uptime. Additionally, incorporating advanced cooling systems, such as liquid cooling or hot aisle/cold aisle containment, can help maintain optimal operating temperatures and reduce energy costs. Overall, a well-planned data center design that takes into account these best practices will result in a reliable and cost-effective solution for handling large volumes of internet traffic.
Bulk internet providers must consider several factors when deploying edge computing solutions. These considerations include network latency, bandwidth requirements, security protocols, scalability, and interoperability with existing infrastructure. By optimizing the placement of edge computing nodes, providers can reduce latency and improve the overall user experience. Additionally, ensuring that edge computing resources are distributed efficiently across the network can help manage bandwidth usage and prevent bottlenecks. Security measures such as encryption, access controls, and monitoring tools are essential to protect sensitive data processed at the edge. Scalability is crucial to accommodate growing demand for edge computing services, while interoperability with legacy systems ensures a seamless integration process. Overall, bulk internet providers must carefully plan and execute their edge computing deployments to meet the evolving needs of their customers and maintain a competitive edge in the market.
Bulk internet providers implement a variety of cybersecurity measures to address threats specific to large-scale data transfers. These measures may include encryption protocols, intrusion detection systems, firewalls, and network segmentation to protect against unauthorized access and data breaches. Additionally, providers may conduct regular vulnerability assessments, penetration testing, and security audits to identify and mitigate potential risks. They may also utilize threat intelligence feeds, security information and event management (SIEM) systems, and endpoint protection solutions to monitor and respond to security incidents in real-time. By employing a multi-layered approach to cybersecurity, bulk internet providers can safeguard the integrity and confidentiality of data during transit and storage.
Bulk internet providers implement fair usage policies for high-volume users by monitoring data usage patterns, setting data caps, and implementing throttling measures to ensure equitable access for all customers. By analyzing traffic shaping techniques, network congestion, and bandwidth management strategies, providers can identify users who are consuming an excessive amount of data and potentially impacting the overall network performance. Through the use of deep packet inspection, Quality of Service (QoS) protocols, and traffic prioritization algorithms, providers can effectively manage high-volume users while still maintaining a consistent level of service for all customers. Additionally, regular audits and reviews of usage patterns help providers adjust their fair usage policies to adapt to changing network conditions and user behaviors.