

Internet backbone routers handle BGP routing updates by exchanging routing information with other routers using the Border Gateway Protocol (BGP). When a BGP router receives an update, it compares the new information with its existing routing table and makes decisions on the best path to reach a specific destination based on factors such as AS path length, next hop, and network policies. These routers use BGP attributes to determine the most efficient route and update their routing tables accordingly.
Internet exchange points (IXPs) play a crucial role in the routing of Internet backbone traffic by providing a physical location where multiple networks interconnect to exchange traffic. By connecting to an IXP, networks can directly exchange traffic with each other, reducing latency and improving network performance. This direct interconnection at IXPs helps in optimizing the routing of Internet backbone traffic by providing more efficient paths for data to travel between networks.
After another busy week last week, the team at Baltic Broadband got the White Stuff & their shiny new shop connected with high speed fibre internet at Liverpool One. Gigabit...

Posted by on 2024-03-05
LCRDC, Baltic Broadband’s new Data Centre brand – has today launched a new Micro data centre, located in the East of Liverpool, based in Edge Hill. Strategically located within the...
Posted by on 2024-03-01
Worried about a possible Fibre Cut? You should be. Though fibre is perceived as a “perfect” media, fibre is fragile and repairs take days or weeks requiring specialist skills and...
Posted by on 2024-02-27
LCRDC, Baltic Broadband’s new Data Centre brand – have today launched a new Micro Data centre located in Bootle, Sefton. Strategically located within South Sefton, this Micro Data Centre is...
Posted by on 2024-02-13
Many would have heard the recent news about the numerous redundancies within the Games Industry. Sadly, there are many more job losses to come, and this will affect many jobs...
Posted by on 2024-02-01
Internet backbone routers prioritize traffic based on Quality of Service (QoS) requirements by using mechanisms such as traffic shaping, packet prioritization, and bandwidth allocation. QoS policies are configured on these routers to ensure that critical traffic, such as voice or video data, is given priority over less time-sensitive data. By implementing QoS mechanisms, Internet backbone routers can meet the performance requirements of different types of traffic and ensure a consistent level of service quality.
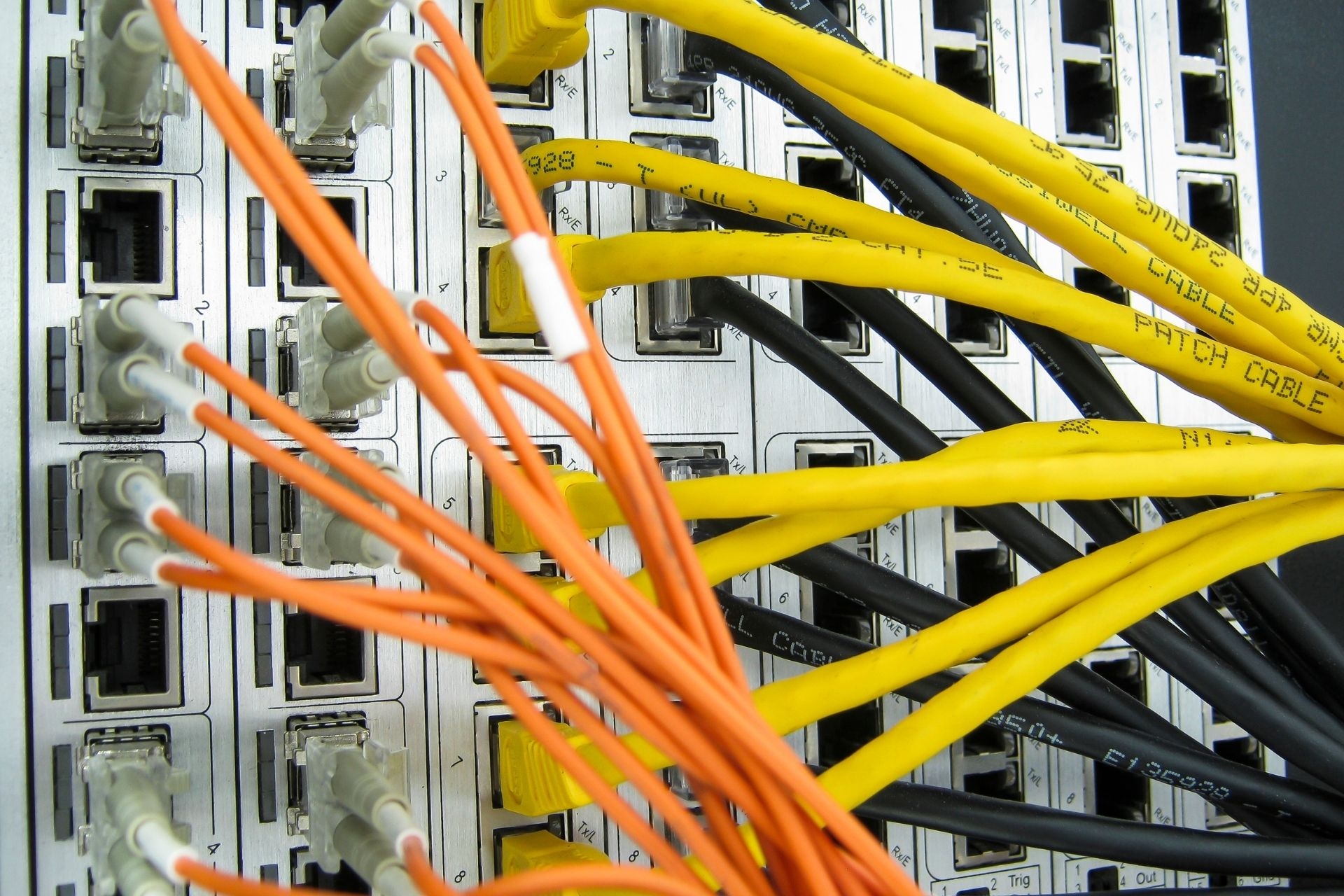
The key differences between interior gateway protocols (IGPs) and exterior gateway protocols (EGPs) used in Internet backbone routing lie in their scope and purpose. IGPs, such as OSPF and EIGRP, are used within an autonomous system to exchange routing information between routers. On the other hand, EGPs, like BGP, are used to exchange routing information between different autonomous systems. IGPs focus on internal routing within a network, while EGPs handle external routing between networks.
Internet backbone routers handle route aggregation to reduce the size of routing tables by summarizing multiple IP prefixes into a single, more specific prefix. This process helps in reducing the number of entries in the routing table, which in turn improves routing efficiency and reduces the memory and processing power required by the router. Route aggregation also helps in minimizing the amount of routing information exchanged between routers, leading to a more scalable and manageable network infrastructure.

To protect Internet backbone routers from DDoS attacks and other threats, various security measures are implemented, including access control lists, firewalls, intrusion detection systems, and encryption protocols. Access control lists are used to filter incoming and outgoing traffic based on predefined rules, while firewalls monitor and control network traffic. Intrusion detection systems detect and respond to suspicious activities, and encryption protocols secure data transmission between routers. These security measures help in safeguarding Internet backbone routers from malicious attacks.
Internet backbone routers handle traffic engineering to optimize network performance and reliability by using techniques such as traffic shaping, load balancing, and path selection. Traffic engineering involves controlling the flow of traffic within a network to ensure efficient resource utilization and minimize congestion. By implementing traffic engineering strategies, Internet backbone routers can optimize the use of network resources, improve overall network performance, and enhance the reliability of data transmission.

Bulk internet data centers have significant environmental impacts due to their high energy consumption, which contributes to carbon emissions and global warming. The cooling systems required to maintain optimal operating temperatures in these data centers also consume a large amount of water, leading to water scarcity issues in some regions. Additionally, the disposal of electronic waste generated by outdated equipment in data centers can pollute the environment if not properly managed. The construction of these facilities can also result in habitat destruction and loss of biodiversity. Overall, the environmental footprint of bulk internet data centers is substantial and requires careful consideration and mitigation strategies to minimize their negative effects on the environment.
Bulk internet providers utilize advanced encryption protocols such as AES, SSL, TLS, and IPsec to ensure secure data transfers for their customers. These providers implement end-to-end encryption to protect sensitive information from unauthorized access or interception. Additionally, they may use VPNs, firewalls, and other security measures to safeguard data during transmission. By employing encryption technologies and following industry best practices, bulk internet providers can maintain the confidentiality and integrity of data as it travels across their networks.
Fiber-optic internet connections typically have lower latency compared to satellite bulk internet connections. This is due to the fact that fiber-optic cables transmit data at the speed of light, resulting in faster response times and reduced lag. On the other hand, satellite internet connections involve data being transmitted to and from satellites in orbit, which can introduce delays in data transfer. These delays are often caused by the distance the data needs to travel and the time it takes for signals to reach the satellite and back. As a result, fiber-optic connections are generally preferred for applications that require low latency, such as online gaming, video conferencing, and real-time data processing.
The future of bulk internet is being shaped by a variety of emerging technologies, including fiber optics, 5G networks, edge computing, and software-defined networking (SDN). Fiber optics, with its ability to transmit data at high speeds over long distances, is revolutionizing the way data is transferred across the internet. 5G networks are enabling faster and more reliable connections, allowing for increased bandwidth and reduced latency. Edge computing is bringing processing power closer to the end user, reducing the need to send data back and forth to centralized servers. SDN is allowing for more efficient management of network resources, enabling greater flexibility and scalability. These technologies are working together to create a more robust and efficient bulk internet infrastructure for the future.
The implications of quantum computing on bulk internet encryption are significant and far-reaching. Quantum computers have the potential to break traditional encryption methods, such as RSA and ECC, by leveraging quantum algorithms like Shor's algorithm to factor large numbers quickly. This poses a threat to the security of sensitive data transmitted over the internet, including financial transactions, personal information, and government communications. As a result, there is a growing need for post-quantum cryptography solutions that can withstand attacks from quantum computers. Researchers are actively developing new encryption algorithms, such as lattice-based cryptography and code-based cryptography, to secure data in the quantum computing era. Additionally, organizations are advised to start transitioning to quantum-resistant encryption protocols to protect their data from potential quantum threats in the future.
The implications of blockchain technology for bulk internet transactions are significant. By utilizing a decentralized and secure ledger system, bulk internet transactions can be conducted with increased transparency, efficiency, and trust. Smart contracts can automate the process, reducing the need for intermediaries and streamlining the transaction process. Additionally, blockchain technology can provide a tamper-proof record of all transactions, ensuring data integrity and reducing the risk of fraud. This can lead to cost savings, faster transaction speeds, and improved overall security for bulk internet transactions. Overall, the adoption of blockchain technology in this context has the potential to revolutionize the way bulk internet transactions are conducted, offering a more reliable and efficient solution for businesses and consumers alike.
Bulk internet streaming services typically require high bandwidth to deliver high-quality video content to users. The bandwidth requirements can vary depending on the resolution of the video being streamed, with higher resolutions such as 4K requiring more bandwidth than standard definition or high definition. Additionally, factors such as the number of concurrent users, the complexity of the content being streamed, and the compression technology being used can also impact bandwidth requirements. To ensure a smooth streaming experience for users, streaming services often invest in robust network infrastructure and content delivery networks to handle the demands of large-scale video streaming. Overall, the bandwidth requirements for bulk internet streaming services are significant and must be carefully managed to provide a seamless viewing experience for users.